|
MonALISA Security Overview
MonaLisa security infrastructure inherits many features from the Globus Security Infrastructure (GSI)
but it also has some own components due to the specific requirements of the system.
Like GSI, MonALISA security infrastructure is based on existing standards: TLS, PKIX and GSS-API.
Securing the access to monitoring data in MonaLISA
Authentication
Identity Certificates and Proxy Certificates
All parties (clients and MonALISA services) of the system use X.509v3 public key certificates for authentication phases.
These certificates are issued by Certificate Authorities and represent the entity identities.
The identity consists of two parts, a unique name and the public x509 key, bound together in a certificate.
The distinguished name contains information about the user such as name, organisational affiliation and email address
and is considered as a unique identifier.
In order to ensure that every party has an unique identity, CA namespace limitations need to be enforced.
That is, policy in the system must deny certificates issued by a authority that are not within the namespace of the this CA
(CA1 can not issue certificates in the namespace of CA2).
In order to integrate with existing grid software (i.e Globus), the MonALISA security architecture allows proxy certificates.
These certificates are short-lived and typically stored with a weaker protection level (stored in clear text and protected only by local file
system privileges).
Authorization
Multiple MonaLisa services may be operated by the same community (group).Group's administators can specify and mantain the policy
governing the access to the monitoring data provided by every MonALISA service in group.
These access control list (ACLs) are managed by a specialized Authorization, Authentication and Accounting (AAA) service.
Using this authorization service the MonaLISA services being part of one group share the same authorization and authentication policies.
To dynamically control ACLs, administators may easily access their group AAA service using a simple secure web-interface.
The authorization is based on the distinguished name (DN) of the subject contained in the certificate and this is information is used
as an unique indetifier when defining an ACL.
Security interactions.
A client accessing monitoring data follows the following scheme:
-
User authenticates to the proxy service using his/her identity certificate. Users operating in a Globus environment can also use their
proxy certificate.
Upon the final of this step the client proved his identity.
-
Based on client identity (Distinguished Name - DN - from approved certificate)the proxy service retrieves the access control list
(rights granted) for this client from the AAA services.
The integrity of the connection between the authorization server and the proxy service checking the authorization information is assured.
Future requests from this client will be filtered based on these ACLs (i.e proxy service acts as a Policy Enforcement Point)
-
Further communication beetwen client and MonALISA services is protected assuring integrity and confidentiality of the messages exchanged.
The scheme is also presented in the following figure.
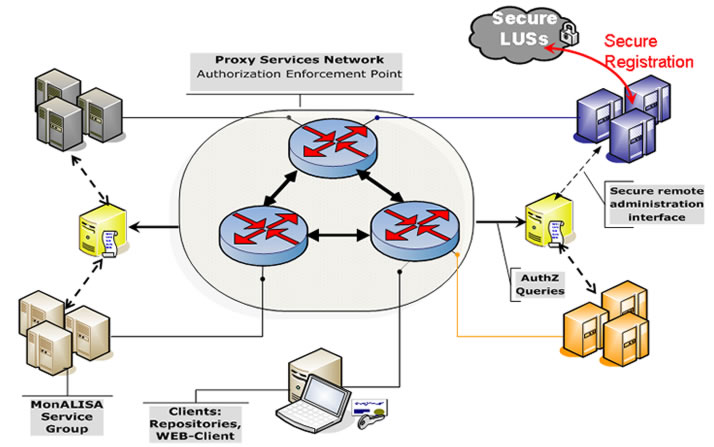
Figure 1: MonALISA Security Infrastructure
|



